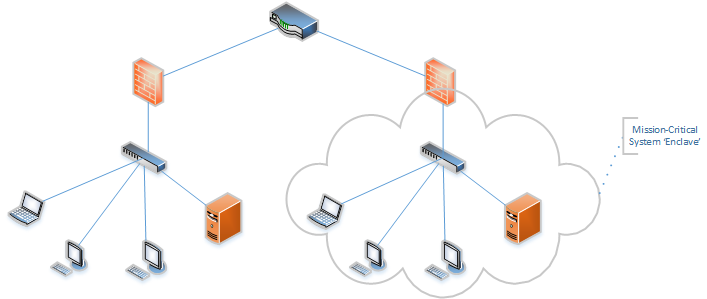
With an ever-growing dependency on cloud technologies, enterprises face increasingly sophisticated threats to their network infrastructure. Cloud network segmentation is emerging as a critical strategy to bolster network firewall security and overall organizational resilience. The core principle behind this approach is dividing a network into multiple segments to circumscribe potential threats and prevent the spread of malicious activities. Cloud network segmentation has advanced to become not just a security best practice but a critical component in the design of scalable, secure cloud architectures. When discussing network firewall security within cloud architecture, we need a strategy to keep up with the fast-paced and ever-changing digital environment. Through carefully crafted network firewall security measures embedded in network segmentation, enterprises can significantly lower their risk profile while enhancing their ability to manage and monitor network traffic.
What is Organization Division?
At its establishment, network division includes partitioning an organization’s traffic into particular sections in light of elements, for example, practical, security, or consistence prerequisites. This precise way to deal with network configuration permits organizations to confine delicate information, oversee traffic streams deliberately, and lessen the potential for unapproved admittance to basic frameworks. Each section, going about as a more modest, more controllable small scale organization, works with the sending of explicit security strategies customized to the traits and requirements of the information it includes. Network division can change a solid and obscure organization game plan into an efficient assortment of secure compartments, each with its strategies and control components. This degree of compartmentalization is basic to limiting the shoot sweep of any single mark of give and take inside the organization geography.
Advantages of Division
The division of cloud networks presents granular command over network assets, prompting a few characteristic advantages. Upgraded security is the essential benefit, as division limits aggressors’ capacity to move horizontally across the organization, lessening the likely scope of a break unreservedly. Also, this division of the organization scene works on administrative consistence by making clear limits around safeguarded information, hence fitting security controls to explicit necessities with more prominent exactness. Execution improvement is another striking advantage. By decreasing cross-section traffic, division eases network clog and works on functional proficiency. The resultant better presentation can essentially upgrade client encounters and the responsiveness of cloud administrations. Besides, according to a regulatory viewpoint, network division structures the organization into additional reasonable blocks, facilitating investigating and organization support.
Executing Division
Decisively executing cloud network division starts with completely understanding the association’s information streams and asset arrangements. This cycle requests obvious accuracy in making division runs and recording network arrangements. Security groups should cautiously plan and plan the format of portions, guaranteeing that each is steady with the one of a kind prerequisites of the information and assets it contains. Setting up network portions is itemized and requests an iterative methodology. Exact and exhaustive documentation is fundamental for this undertaking. It permits groups to have total perceivability into each section and its related conventions, which can smooth out security reviews and consistence surveys.
Access Controls and The executives
When the organization is fragmented, the center movements towards fastidiously overseeing how assets inside each section are gotten to and used. The presentation of job based admittance control and personality the executives inside a sectioned organization characterizes clear limits for client and framework communications in view of restricted admittance and the standard of least honor. Ceaselessly rethinking access control records (upper leg tendons), strategies, and verification processes should be a standard functional method. Customary reviews of these control instruments build up their viability and assist them with adjusting to advancing organization and working environment elements.
Consistence and Division
Network division can tremendously work on an association’s capacity to meet severe administrative necessities that direct exceptional treatment of monetary, individual, and wellbeing data. By segregating such information, organizations can all the more promptly authorize consistence with norms, for example, the PCI DSS for installment information, HIPAA for wellbeing records, or GDPR for the individual information of EU residents. This demonstration of division, thusly, becomes a specialized basic as well as a business one too, moderating dangers of significant fines and reputational harm related with consistence infringement. To this end, standard, coordinated consistence checks are basic, guaranteeing each section sticks to the specified defensive measures. When performed with industriousness, this normal jelly the honesty of the information and the trust of partners who rely upon the association’s capacity to safeguard delicate data.
Observing and Security
Because of their separateness, observing organization portions for security dangers can be testing yet incredibly fulfilling. Network checking devices, including those executing progressed danger identification procedures, are basic for keeping an undeniable level perspective on the organization’s wellbeing and distinguishing possibly compromised hubs inside the cloud framework. Utilizing insight from checking, associations can agilely change security arrangements and division controls to acquire potential security breaks, uplifting the general protection against outer and interior foes. The constantly changing nature of digital dangers requires a similarly unique observing and reaction framework, which must be accomplished through cautious and viable division oversight.
Robotization in Division
Given the fast development of organizations, depending exclusively on a manual division technique becomes impractical. This is where robotization comes in, empowering the consistent implementation and change of organization division at scale. Robotization helps with reliably applying security arrangements across the organization, opening up HR to zero in on essential undertakings that PCs can’t copy. Incorporating robotization advances inside network division processes improves the accuracy and dexterity of organization the executives. As organization conditions fill in intricacy, the advantages presented via mechanized frameworks should be perceived and utilized to guarantee proceeded with network respectability and consistence.
Key Focal points
- Understanding into the basic requirement for cloud network division in current online protection.
- Examining the advantages and vital execution strategies for compelling division.
- Investigating best practices around the executives, consistence, and observing for fragmented networks.
Closing Contemplations
Cloud network division gives a defensive layer that is more imperative than any other time in recent memory in the undeniably cloud-driven, danger loaded computerized scene. Its capacity to group chances and explain controls for particular informational collections makes it fundamental for endeavors looking for vigorous security stances. At last, effective organization division gets from a mix of sound specialized procedure, persistent administration, and an essential appreciation for the job of organization security across the association. By embracing this far reaching approach, organizations can continue onward with certainty, knowing a strong division technique safeguards their cloud assets.